Network Reconfiguration and Robustness
CSC 591: Directed Studies with Dr. Michael Miller
B. Cameron Lesiuk
July, 1998
Department of Mechanical Engineering
University of Victoria, Victoria, BC, Canada
Preamble:
This report was written in partial fulfillment of a CSC 591 Directed Studies course with my supervisor, Dr. Miller. This report was written in Frame Builder and later translated into HTML form.
Click here to return to my home page.
Abstract
This report analyzes several network technologies with a focus on network reconfiguration and robustness. Each network technology is analyzed for its ability to cope with the addition or removal of nodes, changes to link status, and nodes changing network locations. Of the network technologies analyzed, only IPv6 addressed all criteria well.
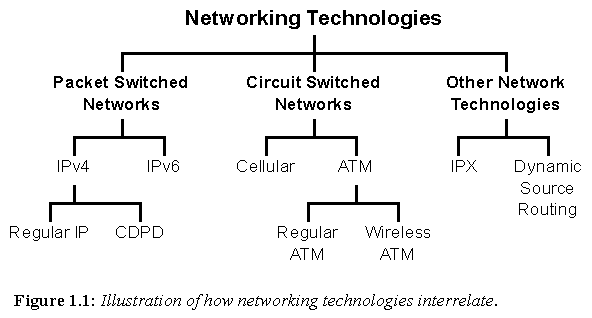
Figure 1.1: Illustration of how networking technologies interrelate.
Figure 2.1: Example of a hierarchical IP network structure.
Figure 2.2: Example of an IP network with loops.
Figure 2.3: Illustration of a CDPD network.
Figure 3.1: Illustration of multiplexed packets (cells) in an ATM transmission.
Figure 3.2: Illustration of virtual channels between ATM nodes.
Figure 3.3: Illustration of circuit routing inside an ATM node.
Figure 3.4: Hierarchical network view of an ATM network.
Figure 3.5: ATM network configuration as seen from node X.B.2.
Figure 3.6: Illustration of a mobile ATM node being handed off.
Table 5.1: Summary of Network Technology Evaluation
Networks are pervasive throughout our world today. The ability for two or more computers to share information is not only useful, but has become commonplace and expected. Just as computers are increasing in speed and capacity, networks are growing in complexity to meet the demands of business and consumers.
The common thread throughout the development of computer networks is the invisibility and seamless integration of the network functionality. The end user, be they at an automatic bank teller or a computer workstation, does not want nor need to understand how information is shared over the network. The only concern to the user is the provision of the network service, encompassing everything from network connectivity (the ability to successfully transmit data from a source to the intended destination) through to robustness and error detection and correction. It has become assumed that networks will operate well, and with minimal human intervention.
With the advent of mobile digital equipment, users began desiring the ability to maintain network services despite changes to their geographical location. Since network topology inherently mimics geography, traditional networks were unable to operate satisfactorily.
Rising to the challenge of providing networking services to a mobile (nomadic) digital device, several networking solutions have been developed. Naturally, the different solutions were designed to different criteria and for different networking technologies. However, they all address the requirement that network services will be maintained despite changes to network topology (geography).
This paper analyzes several current networking technologies which support, or can in some way address aspects of, reconfiguration and robustness in their network operations. This is to say, they maintain network services and connectivity despite changes to network topology. The network technologies analyzed in this paper are grouped according to their philosophy of operation and background, as illustrated in Figure 1.1.

Each networking technology is analyzed for the ability to address three categories of network topology change. The effort required to address the topology change is also analyzed. The three categories of network topology change are as follows:
1) Nodes are added or removed. Network technologies will be evaluated on their ability to provide connectivity to new nodes. Network technologies will also be evaluated on their ability to maintain or otherwise re-route connections impacted by new or removed nodes.
2) Link status changes. Network technologies will be evaluated on their ability to take advantage of new links, compensate for removed or failing links, and find optimal routes to avoid bottlenecks and congestion.
3) Network location changes. A single physical node may, from time to time, change its network location. This is also called a change in the point of access. This often appears as though an old node was removed and a new one was added elsewhere. For many technologies, this results in a loss of any existing connections to the nomadic node at the time of the move. Technologies will be evaluated on their ability to maintain existing network connections to a node despite the change of network location.
In packet switched networks, information is transmitted in small blocks of data called packets [3]. Each packet contains its source and destination network address. Naturally, each node has a unique network address.
A packet en route from its source to its intended destination may pass through many nodes, being forwarded from one to the next. As the packet is transmitted from node to node, each node examines the destination address and makes a decision as to where the packet should be forwarded to next. Ultimately, the packet reaches its destination
In packet switched networks, the resource bandwidth is typically not managed or reserved. It is not uncommon to have messages with different priority, but there is no mechanism by which traffic can be accurately predicted. To avoid bottlenecks and congestion, packets bound for the same destination may be routed along different, less congested paths.
The primary packet switched network technology analyzed in this report is the Internet Protocol (IP). IP has been implemented in a variety of networks, the most popular of which is the Internet. The current version of IP operating on the Internet is version 4, or IPv4. In the following sections, the reconfiguration and robustness of IP under changing network topologies is analyzed. At least one implementation of IPv4 for mobile stations (CDPD) has been developed and will be analyzed as well.
IPv6, the successor to IPv4, is currently being developed and tested by the Internet Engineering Task Force (IETF). IPv6 is currently implemented on a test network of approximately 200 computers. The Mobile IP group of IETF has proposed a networking scheme for nomadic computing devices under IPv6. IPv6 and the Mobile IP group’s solution will be analyzed.
The Internet Protocol (IP) is a mature and well defined packet switched networking technology. Several technologies have been developed and implemented using IP or variations of IP.
In its simplest form, an IP network is arranged as a hierarchy as illustrated in Figure 2.1 [20] [6]. Note that each layer of the hierarchy has its own portion of the address space allocated to it; all nodes below a given network level share the same address prefix. If a source node wishes to send a packet to a destination node, but the two nodes are not directly connected by a link, the packet is transmitted to the node closest to the destination.
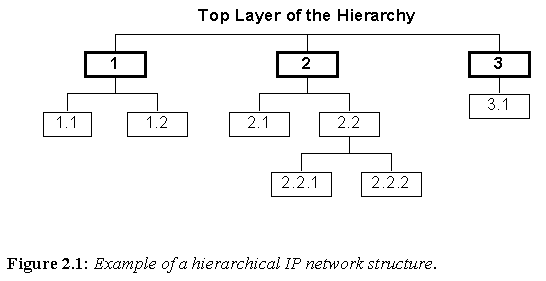
For example, in Figure 2.1, if node 2.2.1 sent a packet to node 3.1, the packet would be sent to node 2.2, 2, 3, and then finally to 3.1 respectively.
By basing network addresses partly on the subnetwork they reside on, IP routing decisions are made relatively simple. Should any node in the network need to send a packet to another node, the routing algorithm can discover which node it should forward the packet to next merely by analyzing the destination network address.
A more practical example of an IP network is illustrated in figure 2.2. In this case, the network has loops.
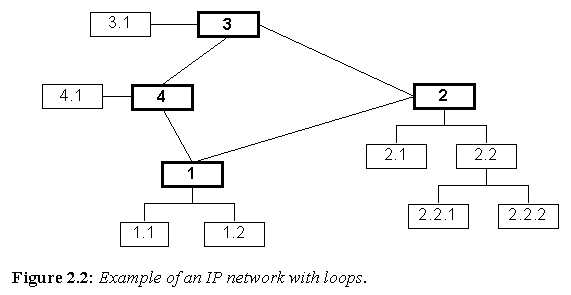
In order to decide where packets should be sent, IP networks utilize routing tables and routing algorithms. In Figure 2.2, node 1 can send packet to node 3 via either of nodes 2 or 4. Node 1 may, by default, send packets to node 3 via node 2. However, should the link between 1 and 2 be severely congested or fail altogether, node 1 may dynamically decide to send packets to node 3 via node 4.
In standard IP networks, each node in the network has a unique network address, in part based on where in the network hierarchy the node resides. When nodes are added or removed from the network, or when links between nodes are created or destroyed, the routing tables and routing algorithms have to be updated.
When a new node is added to an IP network, it must be assigned a unique IP address. This address must reflect the node’s position in the network hierarchy. Under most circumstances, this requires human intervention to initially configure the node. Once a new node has been assigned an IP address, traffic should be able to reach it without any problems; because of the hierarchical nature of IP networks, the IP address will tell other machines how to reach it.
There are provisions under some configurations to provide IP addresses dynamically, such as for dial-in PPP and SLIP connection servers. However, these systems have been "pre-configured" with a pool of valid IP addresses which may be assigned to temporary nodes. Special software is used to manage the IP address pool and update routing tables. Under PPP or SLIP, when a temporary connection is terminated, the IP addresses assigned to the temporary node is recycled.
When a node is removed from an IP network, traffic is merely not routed to it anymore. If the node was the only way to reach other parts of the network, those parts are subsequently cut off as well. If there are alternate routes around the removed node, routing tables (using a protocol such as RIP) will time out or will be automatically updated, adapting to the new network topology. Unfortunately, this can be somewhat slow; until all of the routing tables have been updated or have timed out , network connectivity may be denied. Naturally, where permanent routing tables exist, human intervention is required to manually change the tables.
It is fairly clear from the above discussion that generic IP networks require significant manual intervention to configure and maintain. Adding and removing nodes can be trivial or difficult, depending on the node’s position and importance in the network.
In some cases, where RIP is used, routing tables are automatically updated when critical nodes or links are added or removed. Where RIP is not used, routing tables must be updated manually when links or routers are added or removed.
In the case of a nomadic node, IP has virtually no support. In the simplest case, a nomadic node will appear to the network as a series of node additions and node removals regardless of the method of connection used (PPP, ethernet, etc.). When a nomadic device changes IP addresses as a result of a change in network location, all active connections to the node will be broken and need to be reformed.
CDPD is a digital packet-switched data network on the North American AMPS analog cellular system [17]. CDPD is based on existing data networking standards and on IPv4. The interesting feature of CDPD in so far as this report is concerned is location independence. The CDPD node is independent of service provider and location at which those services are made available. CDPD provides an end-user with a mobile node connected to other CDPD sites or the internet. CDPD implements an IP application programmers interface (API); existing network programs will work unmodified over a CDPD network. This section analyzes how CDPD achieves stationary IP services despite mobile nodes, and how well CDPD meets the criteria outlined in section 1.
The CDPD network uses mostly standard cellular technology. A model of a CDPD network is shown in Figure 2.3.
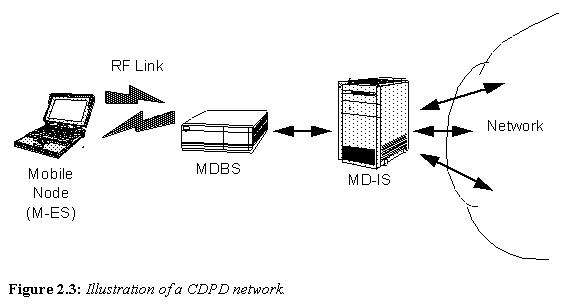
The Mobile End System (M-ES), or nomadic node, is the mobile access point to the network. The nomadic node is free to move from cell to cell without interruption of service. The Mobile Data Base Station (MDBS) is the stationary counterpart which the nomadic node speaks to. The nomadic node will speak to different MDBS’s as it moves from cell to cell. Regular cellular RF frequencies, antennae, and equipment are used for communicating between the nomadic node and the MDBS. The MDBS extracts the CDPD portion of the cellular signal and relays the data on to a central Mobile Data Intermediate System (MD-IS).
The MD-IS is the focal point of CDPD mobility management. The MD-IS is responsible for enabling the nomadic node to move around, and yet appear stationary to the rest of the network. As the nomadic node moves through the mobile environment, the MD-IS tracks it. Therefore, when packets are sent to the nomadic node, the MD-IS always knows how to reach it and knows where to forward the packet to.
The last piece of the mobile puzzle for CDPD is how to handle a hand-off when the nomadic node leaves the jurisdiction of the home MD-IS (i.e.: where the account for the nomadic entity resides). The nomadic node is always associated with its home MD-IS, regardless of where it physically resides in the cellular network. As the mobile moves into different MD-IS jurisdictions, the home MD-IS and local MD-IS negotiate routing information on behalf of the nomadic node. Packets sent to the nomadic node always go to the home MD-IS first. From here, they are forwarded to the current (local) MD-IS serving the nomadic node. The local MD-IS can then deliver the packets to the nomadic node.
When adding or removing nodes to a CDPD network, changes similar to regular IP are required; devices need to be assigned unique IP addresses and routing information needs to be modified (if the M-ES is a router for a subnetwork). Similarly, CDPD is on par with regular IP in its ability to handle added or removed links; routing information needs to be updated, either manually or via an automated process such as RIP.
Where CDPD really shines over IP is when a nomadic node changes physical locations. CDPD accounts for geographical mobility and "hides" it behind an extra routing layers. Since packets sent to a mobile node are always sent to the home MD-IS first, the mobile node appears stationary in so far as the IP network topology is concerned. The home MD-IS tracks the current location of the nomadic node and can always forward packets to it. IP allows packets being sent from the nomadic node to the rest of the network to be routed using conventional routing techniques. Consequently, network connectivity is maintained, despite geography changes, by compensating through the CDPD cellular network and making the nomadic node appear stationary.
The one failing of CDPD is the geography-based limitations of it; if nomadic nodes are regularly outside of the jurisdiction of their home MD-IS, there will always be extra bandwidth being consumed sending IP packets first to the home MD-IS, forwarding them to the local MD-IS, and then finally transmitting them to the nomadic node. This is a sub-optimal solution and only works well if most nodes are expected to remain within the jurisdiction of their home MD-IS.
IPv6 is based roughly on its predecessor, IPv4. As such, many of the issues discussed in previous sections still hold true; IPv6 is a packet-switched networking protocol with routing and network technologies not unlike those found in IPv4. However, IPv6 extends IP capabilities considerably over IPv4, based on the wisdom gained through the extensive implementation and use of IPv4. This is blatantly apparent when analyzing IPv6 for capabilities which allow for the autoconfiguration and management of changing nodes and links. IPv6 is still under development; much of the standard is still in draft format. Fortunately, key components of IPv6 have become RFCs, implying they are now standards.
The first major change in IPv6 is the IP address format [8] [10]. IPv6 network addresses are 128 bits long instead of 32 in IPv4. While 128 bits allows for more unique addresses than there are atoms in the known universe, the address space of IPv6 contains address classifications as well as network location information. In combination, these allow the network address to be significantly more flexible than in IPv4.
For example, in IPv6, it is expected that many network addresses will be assigned to ethernet network devices (which already have unique 48-bit MAC addresses). IPv6 allows for the lower 48 bits of the address to match the MAC address. New or mobile nodes may discover subnetwork address prefixes by listening to broadcast messaging packets [7]. This information can be combined with the ethernet MAC address to create a valid and unique network address. In this manner, a new or mobile node can generate its own valid network address without any external or manual intervention.
IPv6 includes (draft) standard protocols specifically designed to support automatic configuration of added nodes [12] [16] [18]. One such protocol, the Dynamic Host Configuration Protocol (DHCPv6), provides a framework for passing configuration information to IPv6 nodes [4]. It offers the capability of automatic allocation of reusable network addresses and additional configuration flexibility. This protocol has been specifically designed to allow a new node to be rapidly configured and provided network connectivity without human intervention.
IPv6 provides (draft) standard protocols to support IP tunneling [15]. An IP tunnel may be set up between two hosts anywhere on the network. Essentially, local packets intended for a remote node are encapsulated and sent to the remote host via the network tunnel. The remote host receives the encapsulated packets from the tunnel and can reply in kind. Using this mechanism, the remote node appears and behaves as though it were local. This allows remote nodes to derive all the security and service benefits of being a local node.
IPv6 also includes (draft) standard protocols designed to support nomadic and roaming nodes [1] [2] [11] [13] [14]. Each nomadic node is associated with a stationary home address. While situated away from its home, a nomadic node is also associated with a care-of address, which provides information about the nomadic node's current location. IPv6 packets addressed to a nomadic node's home address are transparently routed to its care-of address. The protocol enables IPv6 nodes to cache the binding of a nomadic node's home address with its care-of address, and to then send any packets destined for the nomadic node directly to it at this care-of address. The protocol even specifies an efficient retransmission and binding rediscovery mechanism for when the care-of address changes and cached bindings are no longer valid. In this way, not only does the nomadic node use the same network address, despite changes to its point of attachment, but traffic congestion is avoided at the home address. Furthermore, this networking scheme allows higher level connections to be maintained as the nomadic node changes its point of attachment to the network. append
IPv6 is the only protocol investigated which meets all requirements set out in this report for an automatically reconfigurable and robust network. Added nodes may be configured using DHCP to rapidly gain network connectivity. Network addresses can be assigned by address management nodes, or can even be created using local subnetwork prefixes combined with a MAC layer address. Changes to link capabilities or status are handled similar to those in IPv4, except with increased robustness added to the protocol. Finally, IPv6 incorporates mobile IP capabilities in a fully integrated manner, allowing for nomadic nodes to use a single network address
Circuit switched networks mimic the originals circuit-switched telephony systems used throughout the world. In their basic form, circuit switched networks allow nodes to reserve communication channels to other nodes in the network [9] [17]. Once a reservation, or circuit, has been created, the source node may send a steady stream of data to the destination node, confident the information will arrive and in the same order it was sent, though not necessarily error-free. Once a circuit is no longer needed, it can be removed and the communication capacity is made available to other circuit creation requests.
The means by which circuits are created varies between technologies. The end result, however, is the same. A circuit may pass through many nodes between the source and destination. Each intermediary node knows exactly where to route the information it receives from the circuit. Because circuits are static once established, complex routing schemes are not required. In fact, routing for many circuit switched networks is almost trivial.
The complexity in circuit switched networks comes in the areas of path decision and circuit creation. Each technology addresses this challenge in a different way. The following sections analyze various circuit switched technologies.
The aspects of the cellular voice network relevant to this report are mainly the means by which cellular networks forms and maintains circuits. Therefore, since the cellular is not even a digital network, this section does not go into the details of cellular telephony.
The cellular network is a mobile voice network using both radio frequency channels and land-based lines. A circuit to a mobile node, once established, is maintained despite the mobile’s movement to different "cells" or service areas. This is equivalent to nomadic nodes moving to different network addresses in IP. However, in the case of cellular, not only must network connectivity be maintained, but circuit connections must be maintained in real-time as well.
In its simplest form, cellular is merely a circuit between a mobile node and a base station. The base station is stationary and serves all of the mobile nodes within its cell, or service area. Base stations are set up so their cells overlap slightly. This allows mobile nodes to always be within range of at least one base station.
When a circuit is created to or from the mobile node, the base station allocates an RF channel for use by the circuit. The base station then transmits and receives data to and from the mobile node. This is fine as long as the mobile node remains within the cell (i.e.: within range of the base station). Unfortunately, mobile cellular nodes tend to travel a lot.
When a node moves away from a cell and into a new cell, a cell handoff occurs. The hand off essentially consists of the old base station transferring the circuit to the new base station, thereby maintaining the circuit to the mobile node. What happens behind the scenes is the old base station merely sets up an inter-station circuit to the new base station. Thus the circuit routes through the old station, to the new station, and then to the mobile node. In this way, the mobile node leaves a circuit "trail" wherever it travels. It is assumed (and hoped) by the cellular companies that a given circuit will not persist long enough to form a very long tail.
While the system is simple to visualize when calls are instigated by the mobile node, it is less clear how circuits are created when the destination is the mobile node. To facilitate circuit creation to mobile nodes, the mobile node must always inform the closest base station of its presence. This is called "registering" with the base station. Each time the mobile node moves into a new cell, it registers with the new base station. When a call to the mobile node is placed, the location of the mobile node is thereby known and can be routed to the serving base station.
Because the cellular network is designed to handle many mobile nodes moving between cells, it is extremely good at configuring new nodes and removing old nodes from its routing algorithms. The effort required to configure the network in this case is minimal. Note this is assuming the nodes being added are mobile nodes, not base stations. Base stations employ static routing methods and require substantial manual intervention to be configured.
The cellular network is not so good at handling changes in link availability or usage. As with any circuit switched network, should all available circuits be allocated, new circuits simply cannot be formed.
Naturally, the cellular network is very good at handling nomadic nodes. Each node may move from cell to cell without an interruption in service (assuming the new cell has a free channel). As previously discussed, the circuit, once formed, persists and "follows" the mobile node from base station to base station.
Asynchronous Transfer Mode, or ATM, is a circuit switched digital networking technology. All information is transported through the network in very short (48 data bytes plus a 5-byte header) packets called "cells". Information flow is along paths (called "virtual channels" or circuits) set up as a series of points through the network. The packet header contains an identifier which links the packet to the correct path for it to take towards its destination. Packets on a particular circuit always follow the same path through the network and are delivered to the destination in the same order in which they were sent.
An ATM packet is not unlike a packet in a packet switched network. A block of user data is broken up into packets for transmission through the network. But there are significant differences between ATM and packet switched networks.
Firstly, ATM packets are a fixed length, no more and no less. In packet switched networks the packet size is a fixed maximum but individual packet size may vary.
Secondly, ATM packets are a lot shorter. A single ATM packet does not need a complicated header which can be referenced to make routing decisions. ATM packet headers only contains a pointer to a pre-configured circuit and a checksum. There is other information in the ATM packet header, such as priority bits, but it is not relevant to this report.
Lastly, ATM packet sequence is preserved and every packet follows the exact same route through the network. Both sequence preservation and routing are characteristics of circuit switched networks. This differs greatly from a packet switched network where, in some cases, every packet may take a different route to the destination, and may be duplicated (several copies of the same packet arrive), arrive out of order, or not arrive at all.
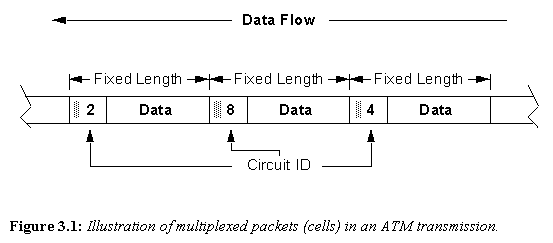
An example of a series of multiplexed ATM packets transmitted down a single physical link is shown in Figure 3.1. Note packets belonging to different logical connections, identified by the virtual channel (VC) or circuit ID, are transmitted one after the other on the link. The multiplexing is not fixed, however, requiring each packet to contain a circuit ID field in its header. In practice, ATM also specifies concepts for virtual paths, virtual channel links, etc.. However, for this report, the concept of a single circuit ID identifying a route through the network is adequate.
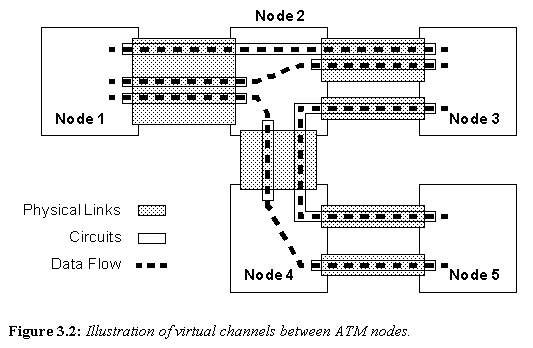
The key concept in ATM is related to how data is routed through the network. Figure 3.2 shows an example of the circuit concept in an ATM network. At each node in the network, packets are routed based on their circuit ID. Each available circuit between two nodes has a number associated with it. Figure 3.3 shows how a node will select the next link for a packet to be sent down. A simple lookup table of active circuits allows all of the data to be properly routed with very little delay.
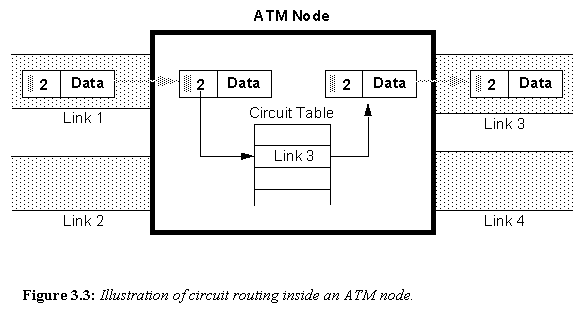
At each node, the circuit lookup table is referenced which tells the node which link to send to packet to next. The circuit tables are constructed when the circuit is created.
For example, the data packet in Figure 3.3 is travelling down circuit 2. It arrives at the node illustrated from the physical link 1. The circuit table instructs the node to forward the packet to physical link 3.
The key routing algorithm in ATM is related to the method used to construct and maintain circuits. This topic is addressed in the following sections. Section 3.2.1 analyzes channel creation for stationary ATM networks. Section 3.2.2 analyzes channel maintenance in wireless and ad-hock networks.
The ATM routing mechanism is a combination of source routing and dynamic routing. Routing is only used during circuit creation; once a circuit is established, the circuit path through the network is permanent until the circuit is removed [9] [19]. To facilitate source routing, where the source node decides the path to be taken through the network, each node has to maintain a complete view of the network.
At the heart of ATM routing is the concept of a routing hierarchy. Every node in an ATM network has some form of a view of the entire network. An example of an ATM network can be seen in figure 3.4. The figure shows three different views of the same network.
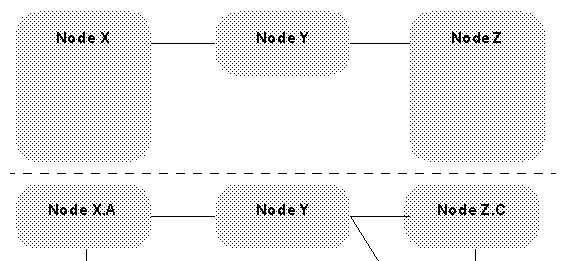
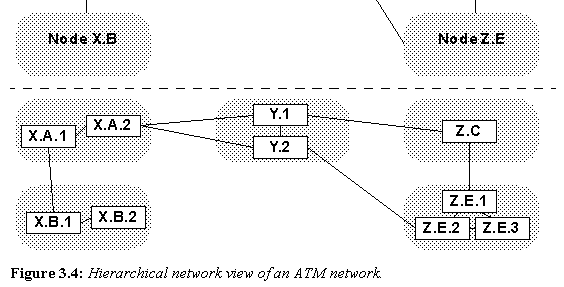
Because storing and maintaining the entire detailed network topology in every node would be difficult if not impossible, each node instead only maintains the level of network detail required to achieve its source routing. Specifically, each node only maintains knowledge of its peer nodes and the peer subnetworks above it in the network hierarchy. Figure 3.5 shows what the network of Figure 3.4 looks like to a single node (in this case, node X.B.2).
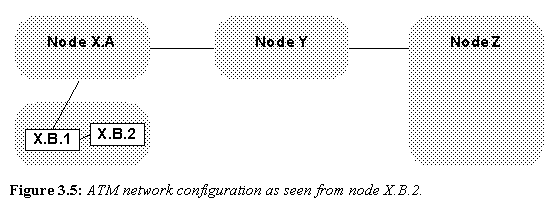
In the above network, when X.B.2 needs to route a circuit through to Z.E.1, it may route the network in the following manner: X.B.2 to X.B.1 to X.A to Y to Z. Note each time a subnetwork boundary is crossed, the next hop in the route "uplinks" to the next higher hierarchy layer. As the circuit is actually routed through X.A, Y, and Z to the final destination, those subnetworks are responsible for finding exact routes through themselves to facilitate the circuit creation. In this way, the further a subnetwork is from a node, the less detail the node needs to know about it. This balances the requirements of source routing with the problems of knowing the total network topology.
When a channel is routed through a subnetwork layer at which no single node can be identified (e.g.: layers X.A, Y, and Z in the above examples), a single node is designated to act on behalf of the subnetwork. This node is called the group leader. This node maintains the subnetwork’s presence at the higher network layers and enables the subnetwork to appear as a single node to other subnetworks when calculating source routes. This structure is recursive and repeats itself as each higher layer is formed.
In regular ATM, adding or removing nodes must be done manually. The ATM standard provides a mechanism by which a node can discover and maintain knowledge of its neighbors and links. However, for this mechanism to operate properly, nodes must be configured with network addresses which conform to the ATM address structure.
Once all nodes have been assigned proper network addresses, the nodes will discover links and neighbors themselves. This process is recursive, just like the subnetwork addressing scheme, so that subnetworks will also discover their neighbors and links. This continues until the top-most layer is completely described to each node in the network. This eliminates the need to create and maintain complex routing tables as found in packet switched networks.
Removing a node from an ATM network is simple as long as the node is not a group leader for a subnetwork. Normally, information of the node’s removal will propagate throughout the subnetwork and circuits will no longer be routed through the node. Note any existing circuits through a node when it is removed will be lost.
Adding or removing links in an ATM network is similar in effect to adding or removing a node; information regarding the link’s status will be automatically propagated throughout the network. Any existing channels through a link when it becomes congested or is removed will be lost.
ATM is intolerant of nomadic nodes in a similar way to IP. A nomadic node, as it hops from subnetwork to subnetwork, changing its point of access and network address each time, will lose all existing connections (circuits) with each hop. To make matters worse, no standard ATM procedure is defined to allocate a network address to a nomadic node each time it changes its point of access. This means as the node moves from point to point, it must be manually reconfigured to use a network address suitable to its location. These restrictions render ATM inadequate to maintain connections to a nomadic node through changes in the point of access.
Wireless ATM was designed to provide ATM network connectivity to wireless mobile nodes. There are several ATM technologies which provide different aspects of automatic configuration and robustness [19]. The general scheme used for a wireless mobile ATM node is analyzed in this section.
Because changing network addresses for an ATM node results in a loss of existing connections to the node, wireless ATM provides the ability for a single physical ATM node to keep its network address despite changes to its point of access to the network. The ATM network maintains network connectivity through a technology which resembles a combination of Mobile IP with cellular hand-off operations.
Figure 3.6 illustrates a mobile ATM node as it changes its point of access to the network.
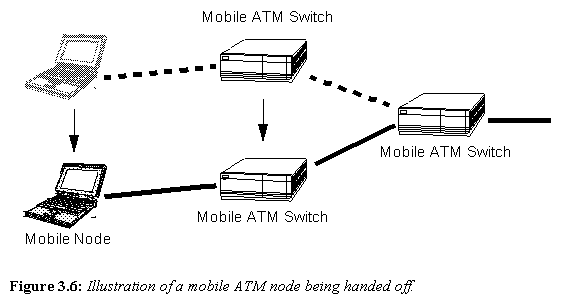
Note in the above example the Mobile ATM Switches are capable of complicated routing methods and "track" the mobile node in much the same way the cellular network operates. As the node changes its access point, network connections and services are handed off to the next nearest Mobile ATM Switch.
Ultimately, the mobile ATM network may interface to a regular ATM network. This point of access to the regular ATM network remains constant and, in essence, hides the mobility aspect from the rest of the ATM network.
Wireless ATM still requires nodes to be properly identified with a valid network address before they can operate. For nodes being added to the network, this requires manual configuration. Once the network address is assigned, however, the network will automatically adjust to provide and maintain network connectivity to the node.
For nodes being removed from the network, the operation is similar as for regular ATM networks; information regarding the removal of the node propagates through the network and services to the node will be removed.
Wireless ATM responds to changes in link status similar to regular ATM. For mobile nodes changing their network point of access, link removal and creation is a regular process; the Mobile ATM Switches hand-off the connection information for the mobile node to the next nearest Mobile ATM Switch.
Wireless ATM adds the protocols and standards to ATM to facilitate rerouting when a mobile node moves. Using this method, wireless ATM maintains network connectivity for mobile nodes. However, should the Mobile ATM Switches themselves change, the effect is the same as for regular ATM networks; existing circuits are lost and the node "disappears" from its first location, and a new node "appears" in the new location.
As this paper was being researched, several interesting and relevant technologies were found. However, for one reason or another, these technologies did not fit the main stream focus of the paper. Nonetheless, it was considered useful to include some mention of them to document their contributions. These technologies are presented in the following sections.
IPX is a proprietary network protocol developed and owned by the Novelle Corporation. IPX is a packet switched network [17]. However, unlike IPv4, IPX addresses contain two parts: a network address, and a MAC layer address. Obviously, for ethernet interfaces, the MAC address matches the ethernet interface’s MAC address.
By using the MAC address as part of the node address, a new node added to an IPX network merely needs to discover the network address on which it resides. The node can combine this information with its MAC address to form a valid IPX address for itself. While this does not help maintain connections for nomadic devices, it does simplify the task of configuring new nodes.
This is not unlike the IPv6 addressing scheme. However, as IPX is much older than IPv6, it is the suspicion of the author that the designers of IPv6 got the idea from IPX.
As discussed in previous sections, source routing is a routing technique in which the sender of a packet determines the complete sequence of nodes through which the packet is to flow. The sender explicitly lists this route in the packet's header, identifying each forwarding "hop" by the address of the next node to which to transmit the packet on its way to the destination node.
Dynamic Source Routing (DSR) is a proposed routing technique for ad-hock networking environments which experience frequent topology changes [5]. DSR offers a number of potential advantages over other routing protocols for mobile ad hoc networks. First, DSR uses no periodic routing messages (i.e.: no router advertisements and no link-level neighbor status messages), thereby reducing network bandwidth overhead and avoiding the propagation of potentially large routing updates throughout the ad hoc network. The DSR protocol is able to adapt quickly to changes such as host movement, yet requires no routing protocol overhead during periods in which no such changes occur.
DSR is a combination of circuit switched and packet switched technologies. When a node wishes to send information to another node in the network, it broadcasts a routing request message. This message is forwarded by each node until every node in the network has seen the request. Route packets are then returned to the original node describing the various (shortest) paths from the source to the destination.
Once a path is discovered in this way, the source node can send packets directly to the destination node. In each packet header, each node in the path is specified in the order it will receive the packet. As each node in the path receives the packet, the node merely reads the next node’s address from the header and forwards the packet to that node.
DSR has many advantages from the viewpoint of this report. Nodes being added to or removed from the network do not affect the network in any way until packets are sent to or from them. The only criteria for network addresses is for each node to have a unique address; no address structure or hierarchy is required.
Changes to links because of link or node changes may require new paths to be discovered. Link additions require no overhead and will not be used until new paths are required. Link removals or congestion may cause paths to become inadequate or invalid, requiring the source to rediscover a new path to the destination.
DSR does not tolerate nomadic nodes. Since connections are based on static paths through the network, should any given point in the path move to a different point of access, the static path may become invalid and a new path recomputed. However, since all nodes in the network have unique network addresses, and the network does not require any special structure, nomadic nodes are not "cut off" from network services when they move; after the initial delay of recomputing new paths to the mobile node at its new location, network connections can be re-established.
The network technologies surveyed for this report have varying degrees of support for reconfiguration. Robustness also varies somewhat from technology to technology, depending on whether nodes are being added, removed, links are changing states, or nomadic nodes are moving their point of access. Table 5.1 contains a summary of the technologies and a rough indication of their ability to meet the specified criteria.
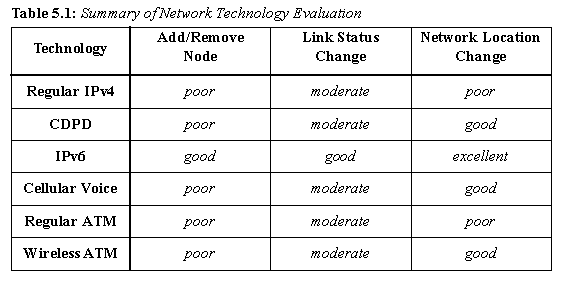
Some technologies, such as IPv4 and Wireless ATM, manage link additions and removals elegantly and efficiently. Other technologies, such as the cellular network or CDPD, are strong at managing nomadic nodes.
Of the technologies surveyed, only IPv6 excels in all of the criteria for a reconfigurable and robust network. IPv6 is by no means the smallest or simplest specification analyzed in this report. It does, however, have one of the most complete specifications. Furthermore, it has the advantage of building upon its mature and well-understood predecessor, IPv4.
For further research and understanding into the operations of reconfigurable and robust network technologies, it is recommended that IPv6 be used both as a guide and a basis by which other technologies can be measured. It is recommended that IPv6 be investigated further to expand knowledge and understanding in reconfigurable and robust networks.
[1] Bernard Aboba, Mark A. Beadles, "The Network Access Identifier," Work in Progress, Microsoft Corporation, CompuServe Network Services, 25 February 1998.
[2] Bernard Aboba, Glen Zorn, "Roaming Requirements," Work in Progress, Microsoft Corporation, April 1998.
[3] Richard Barnett, Sally Maynard-Smith, Packet Switched Networks: Theory and Practice, Sigma Press, 1988.
[4] J. Bound, C. Perkins, "Dynamic Host Configuration Protocol for IPv6 (DHCPv6)," Work in Progress, Digital Equipment Corp., Sun Microsystems, 13 March 1998.
[5] Josh Broch, David B. Johnson, David A. Maltz, "The Dynamic Source Routing Protocol for Mobile Ad Hock Networks," Work in Progress, Carnegie Mellon University, 13 March 1998.
[6] Douglas E. Comer, David L. Stevens, Internetworking with TCP/IP Volume II, Prentice-Hall, 1991.
[7] A. Conta, S. Deering, "Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification," RFC 1885, Digital Equipment Corporation, Xerox PARC, December 1995.
[8] S. Deering, "Internet Protocol, Version 6 (IPv6) Specification," RFC 1883, Xerox PARC, Ipsilon Networks, December 1995.
[9] Harry J. R. Dutton, Peter Lenhard, Asynchronous Transfer Mode, Prentice Hall, 1995.
[10] R. Hinden, S. Deering, "IP Version 6 Addressing Architecture," RFC 1884, Ipsilon Networks, Xerox PARC, December 1995.
[11] David B. Johnson, Charles Perkins, "Mobility Support in IPv6," Work in Progress, Carnegie Mellon University, Syn Microsystems, 13 March 1998.
[12] Charles Perkins, "Extensions for the Dynamic Host Configuration Protocol for IPv6," Work in Progress, Sun Microsystems, 13 March 1998.
[13] Charles Perkins, "IP Mobility Support version 2," Work in Progress, Sun Microsystems, 12 November 1997.
[14] Charles Perkins, David B. Johnson, "Route Optimization in Mobile IP," Work in Progress, Sun Microsystems, Carnegie Mellon University, 20 November 1997.
[15] Charles Perkins, David B. Johnson, "Special Tunnels for Mobile IP," Work in Progress, Sun Microsystems, Carnegie Mellon University, 20 November 1997.
[16] Luis A. Sanchez, Gregory D. Troxel, "Rapid Authentication for Mobile IP," Work in Progress, BBN Technologies, 21 November 1997.
[17] Mark S. Taylor, William Waung, Mohsen Banan, Internetwork Mobility: The CDPD Approach, Prentice Hall, 1997.
[18] S. Thomson, T. Narten, "IPv6 Stateless Address Autoconfiguration," RFC 1971, Bellcore, IBM, August 1996.
[19] C-K Toh, Wireless ATM and Ad-Hoc Networks, Kluwer Academic Publishers, 1997.
[20] "Internet Protocol," RFC 791, Information Sciences Institute, September 1981.
Connection
For the scope of this report, a connection is an active statefull network condition in which two or more nodes have agreed to exchange data in a coordinated maner. For IP, connections are formed by higher level protocols such as TCP, and are therefore not discussed in this report. However, it is nonetheless relevant to examine how connection-based protocols are affected when analyzing networks for reconfiguration and robustness.
Layer
For the scope of this report, a layer is a loosely defined network or application layer. Unless specific model layers are relevant in a given context, no specific network layering model is implied or used.
Link
For the scope of this report, a link represents a physical medium accross which information can be communicated between two nodes in a network.
Mobile
See "nomad".
Network
A network is a collection of two or more nodes able to communicate over links between them.
Node
Any communication intermediary or end point in a network is a node. Links connect nodes and allow them to exchange information. For the scope of this report, nodes are generic networking or computing devices and can be routers, end points, or switches.
Nomad
In the context of this report, the terms "nomadic" and "mobile" are used interchangeably. They have subtlely different meanings in general, but for this report, the network effect is the same: the point of access or network topology is changed.
Packet
For the scope of this report, the unit of information transfer for the protocol in context is referred to as a packet. Note this may vary from the technology-specific lingo. For example, where IP would properly use the term "datagram", and ATM would use "cell", this report uses the generic term "packet".
Router
Any node which is responsible for deciding, forwarding, and/or changing packets flowing through the network.
Subnetwork
A subnetwork, or just subnet, is a sub-portion of the network which shares something in common. Often, a subnetwork will share an address space.